Secure mobile working from any device, anywhere
Microsoft 365 Office applications are ubiquitous. Hackers don't use such difficult words to attack your business. One click on an email, a Word, an Excel file or a SharePoint link is all it takes.
Microsoft offers a broad scale of configuration settings and functionalities to protect your Office 365/Microsoft 365 tenant, or at least parts of it. We ensure that you use them to the fullest, complemented by advanced technologies where necessary.

Microsoft 365 security audit
Do you know your weak spots? Let us help you get insights in your current situation. Our Microsoft 365 security audit is a profound security audit with a special focus on your Microsoft 365 ecosystem.
Take a head start with the Microsoft Secure Score
You are surely familiar with the Microsoft Secure score. It gives you a score about your security posture, and provides tips on how to improve it. At many companies this score is very low and the various "tips" can quickly become too much or redundant. The right questions arise: do I really need all this? What do I expect from my security policy? What are the pros and cons? We can help providing the the answers.
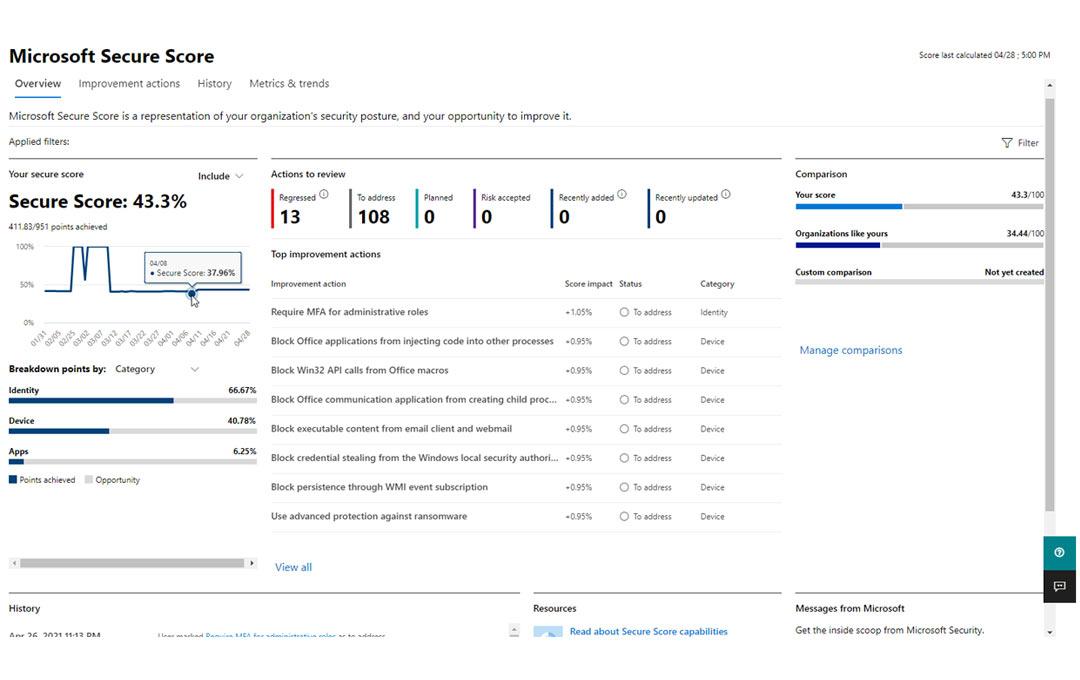
Easi's Microsoft 365 Security assessment toolkit
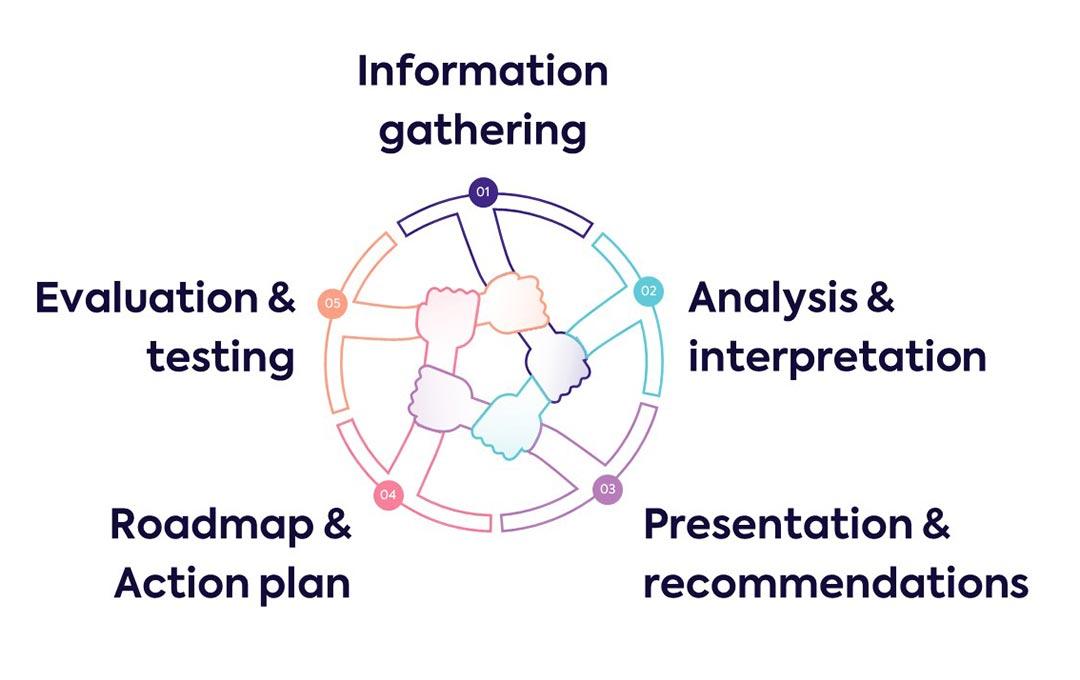
Our security assessment kit goes beyond offering tips. In addition to your Microsoft secure score, we perform an audit of your Microsoft 365 tenant (Identity, roles, mailboxes, subscriptions, devices, etc). We check how your security policy is set up and draw up a roadmap with clear actions based on the scope that you have indicated. Performing such an audit annually is not a luxury.
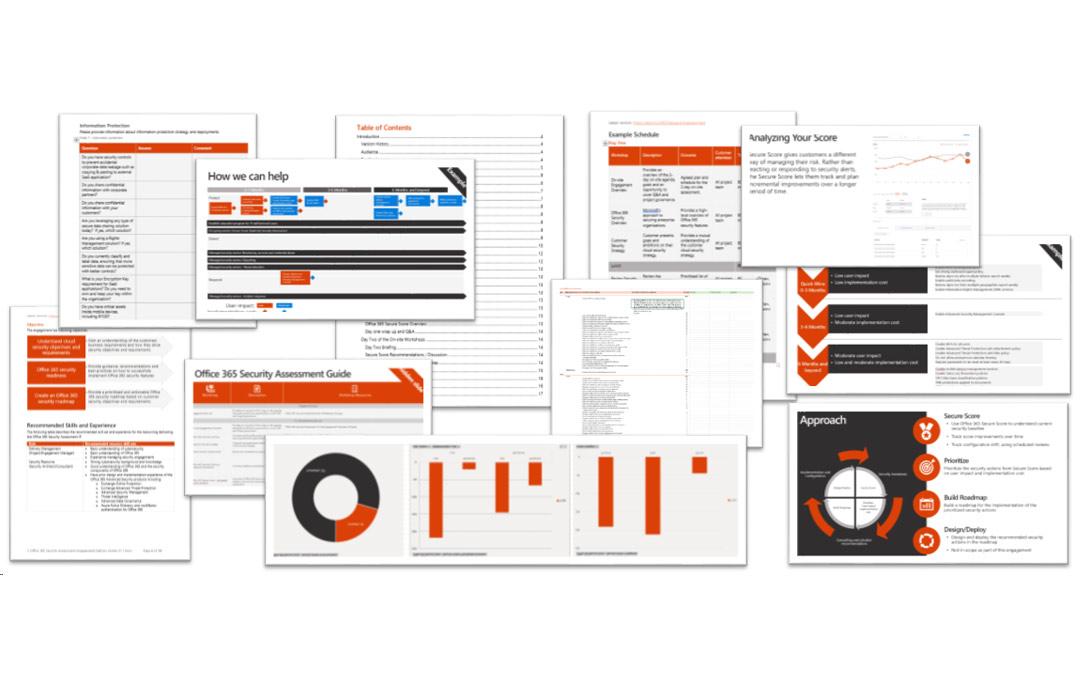
Close the cybersecurity gaps in Microsoft 365 at your pace
The end result of this security assessment is a clear roadmap of areas for improvement that will help you better secure your cloud, on-prem or hybrid Microsoft environments. Starting from quick wins completed by short- and mid-term changes to make your organization cyber-proof. Whether you implement these changes, when and by us or by yourself, is entirely up to you.
"The Microsoft security audit was an absolute added value for us. Easi's consultants had a good sense of our situation and were able to quickly point out clear quick-wins for us. Since the audit, the security of our environment has gone up and we have a more comfortable feeling that the potential risks have been properly identified."
Bart Maes - ICT-manager at Mathieu Gijbels

You want to get insights in your companies security posture?
Don't wait until it's too late.
Microsoft managed services
In our Microsoft managed service offerings, we take into account the ever-changing business challenges. Both applications and the people who use them benefit from the expertise of our highly regarded Microsoft experts during coaching sessions, workshops, assessments and audits.
Pro-active monitoring, analytics & remediation go hand in hand with on-call services, for any customer requests, going from simple daily tasks to more complex configurations. All activity is constantly monitored & analysed to constantly improve the collaboration process.

Pro-active services
With our proactive services, we provide peace of mind in your day-to-day use. By responding to cyber threats from the outside as well as those from within your organization.
- Access control: We manage via Intune and Azure AD who and/or if someone gets access to applications, documents, passwords, etc. Everything is linked to the online identity of your employees so as not to hinder them in their daily use.
- Data security: Our best of breed positioning allows us to incorporate both Microsoft and other advanced technologies to secure your data. And this on any device, anywhere via cloud services or on-premise.
- Periodic review: We check repeatedly and at appropriate times whether your security posture is still up-to-date with the changing market. We take a fresh look at internal factors such as your company situation and policy, but also at licenses and external factors such as risk in and outside Microsoft 365.
- Intelligent monitoring: With Azure Log Analytics, we consolidate various audit logs in Microsoft 365. Sophisticated rules will ensure that we are alerted to possible threats. Helped by Microsoft Intelligent Security Graph we will respond appropriately (automatically), proactively or reactively, as you wish.
On-call services
We not only provide answers to questions, but also assist you with advice and assistance with phone support or ticket based support. This can arise from our own monitoring actions or at your request. We relieve your own IT department by having Microsoft specialists carry out the operational management of certain tasks. This allows your IT department to focus on their priorities.
We have certified competencies in various domains:
- Azure AD
- SharePoint
- Teams
- Security certifications
- Exchange Online
Microsoft's environments are constantly evolving, just like your business needs. That is why our experts are trained to think along with your business operations and to look for constant improvements. Both security configurations and new features in your subscriptions will first be analyzed and tested extensively, after which they will be implemented in consultation with you. All this always fits in the roadmap we defined for you.
To keep not only your licenses up to date but also your users, we also offer End user awareness trainings: Through hands-on educational trainings, they are made aware of the possible dangers and how to deal with them. And in order not to leave anything to chance, we also test whether they have learned anything thanks to the Phishing test.
They already trust us
Additional security services
Security Awareness Trainings
To keep not only your environment up to date but also your users, we offer end user security awareness trainings: Through hands-on educational trainings, they are made aware of the possible dangers and how to deal with them.
Phishing campaigns
In order not to leave anything to chance, we also test whether your employees have learned anything thanks to our phishing tests: do they click on risky attachments or hyperlinks? How likely are they to fill in sensitive data in shady webforms? Our Phishing campaigns will give you the insights.
Ethical hacking
Our team of ethical hackers can be activated in case of advanced, complicated situations with lots of custom development on Microsoft 365. Using ethical hacking techniques, they will try to discover vulnerabilities in your environment and report about them.












