We are also there for you when your systems fail.
Intervening quickly and efficiently when a cyber incident occurs can mean the difference between a minor disruption or a longer and costly interruption resulting in possible reputation damage.
Incident response team as a service
Easi offers a team (CSIRT) of certified experts to detect, investigate and remediate incidents. With our cyber forensics and recovery support, we draw lessons from the incident to make you even more secure for the future.
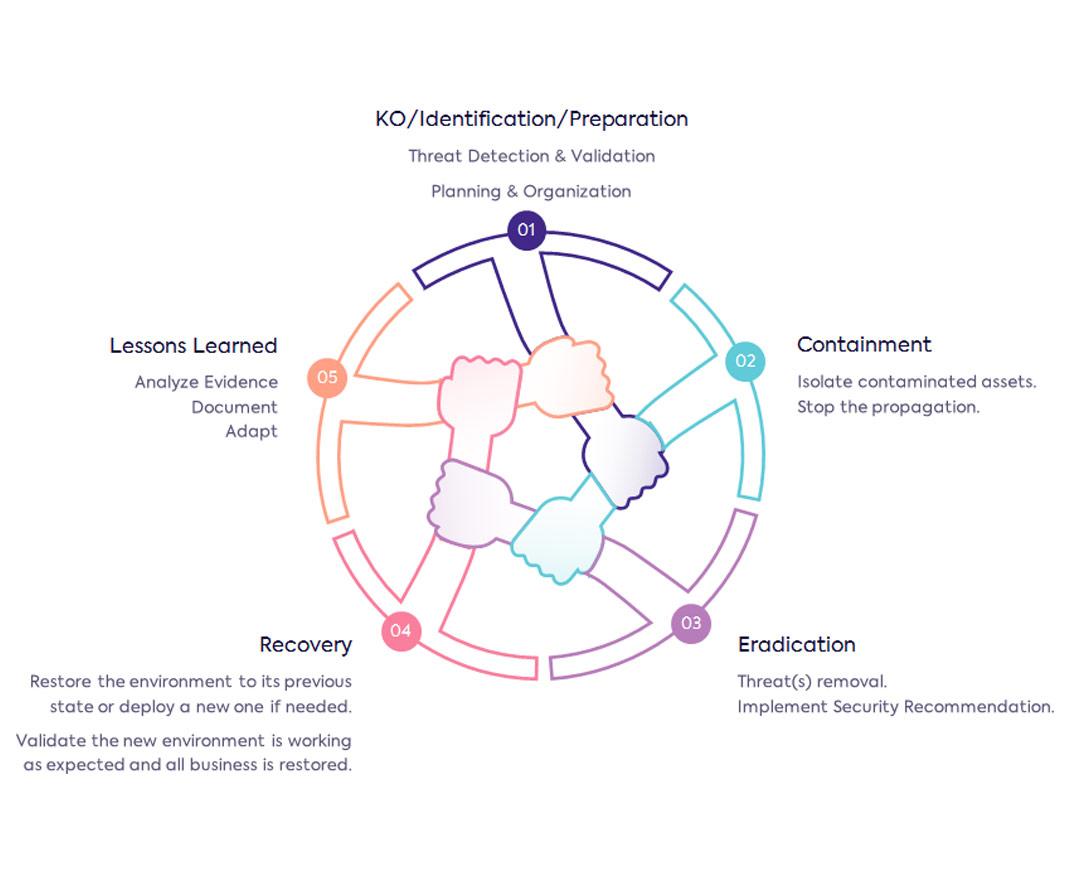
What is Cyber Forensics and when is it useful?
You might find yourself in one of the following scenarios:
- You have a defective hard drive containing critical information.
- A virus has devastated your network, infecting dozens of clients.
- End user data, protected under GDPR, has been compromised, and you don't know how to react or who to inform.
- You suspect the theft of intellectual property by one of your employees but you don't have proof.
- Some of your servers are behaving strangely and you cannot find the cause.
With cyber forensics techniques, we can help you understand what is happening, and through incident recovery, we help you fix it.

First aid for ransomware and other attacks
Under attack? Or do you want to know more about Ransomware and what you need to do in case of a cyber incident?
Cyber Forensics use cases
Data loss
Valuable data was lost, maybe due to a cryptolocker virus, a failed hard drive, or through accidental deletion.
Data theft
Sensitive data was accessed without permission and you are looking for the what, who, when, how, or maybe for proof to take (legal) action.
Outage
Important data or services went down under suspicious circumstances and you need help brining them (safely) back online.
Incident response
Forensics analysis
How did the hacker get inside the network? Who accessed these files in the last month? How did the virus spread between clients? And so on. Our Forensics analytics specialists will go after all the details needed to recover and protect your systems for the future.
Data recovery
We will attempt data recovery from defect or wiped storage media, from crypto locker viruses, or from accidental deletion processes. Our highly skilled professionals will go the extra mile to recover your data as completely as possible to bring your systems back to normal.
Infrastructure Recovery
We erase viruses, restore systems, close security holes and support you in preventing future incidents. We can advise your IT team on best practices or take over the full security management of your environment in a managed services agreement.
GDPR Consultancy
With our in-house ISO27001 and GDPR expertise, we recognize when certain actions must be taken and help you remain compliant in your data protection journey. Our CISO as a service offerings can be an excellent choice to get in the right direction.







